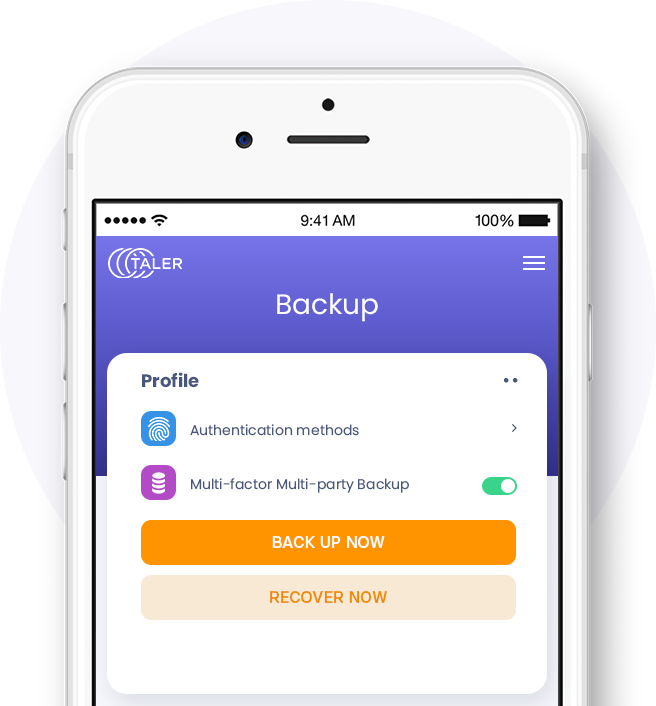
Benefits of Anastasis
Anastasis is a key recovery system that allows the user to securely deposit shares of a core secret with an open set of escrow providers, to recover it if the secret is lost. The core secret itself is protected from the escrow providers by giving each provider only part of the information, and additionally by encrypting it with an identity-based key unknown to the providers. Anastasis is a GNU package.
The Problem
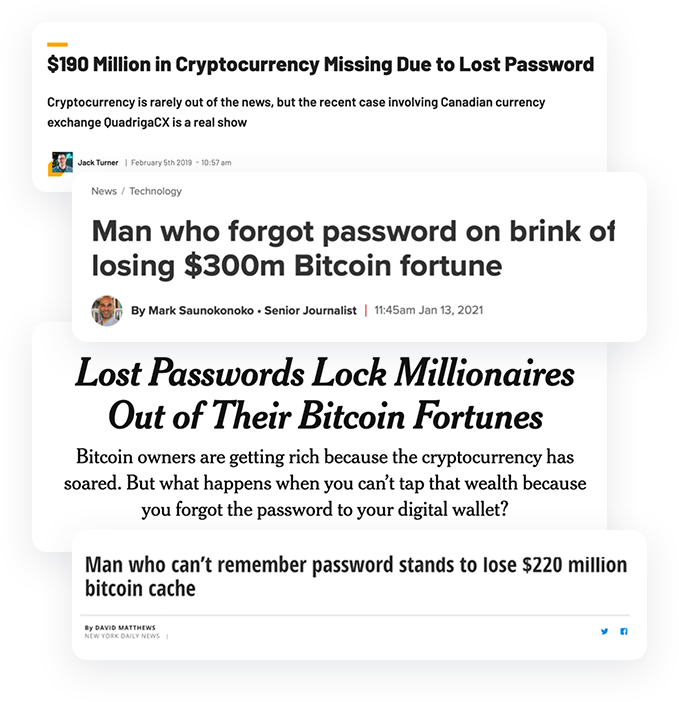

Confidentiality requires only consumer is in control of key material.
Cryptographic key-splitting solutions so far are not usable.
Consumers are unable to simultaneously ensure confidentiality & availability of keys.
European e-money issuers using electronic wallets must:
- Enable consumers to always recover their electronic funds (i.e. if devices are lost).
- Not assume consumers are able to remember or securely preserve key material.
The Solution
Users split their encrypted secrets across multiple service providers
Service providers learn nothing about the user, except possibly some details about how to authenticate the user
Only the authorized user can recover the key by following standard authentication procedures (SMS-TAN, Video Identification, security question, e-mail, etc.)
The Concept
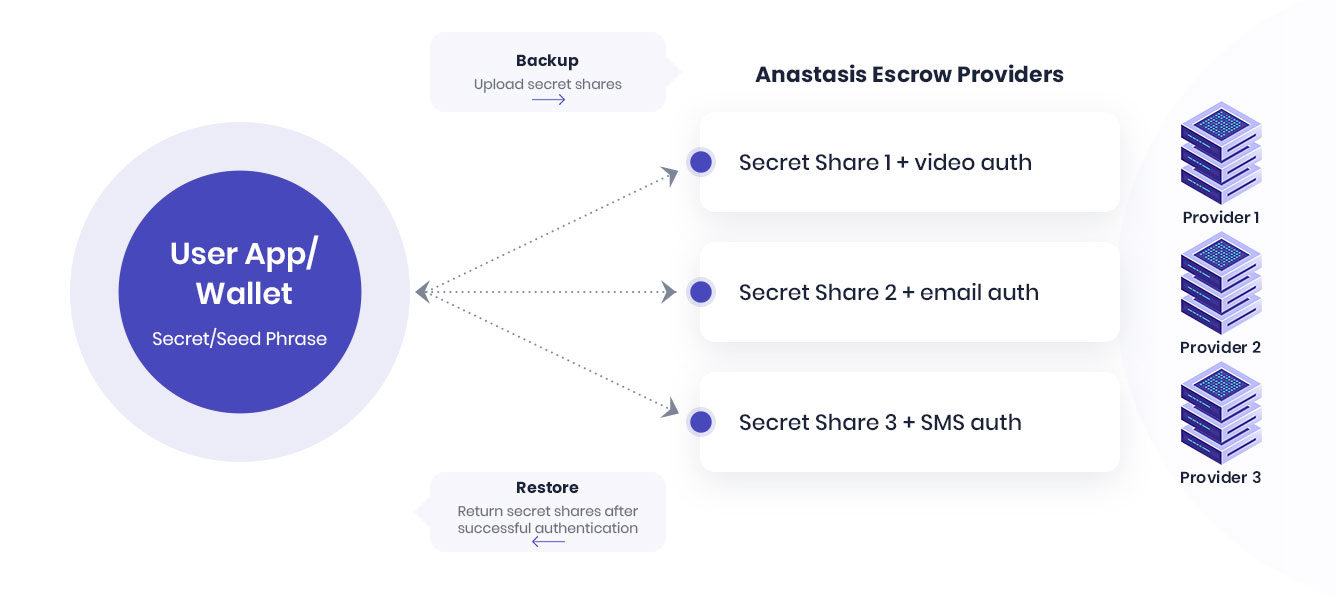
Flexible
Anastasis lets you save your secret on several escrow providers. You can choose different combinations of these providers to recover your secret. The various providers provide different authentication methods (like SMS, secure question or E-Mail) which the user has to supply to recover their secret.
Defense in depth
Anastasis is based on well-known cryptographic techniques. Our resulting solution offers post-quantum security. A compromised database of an individual Anastasis service provider by itself never leaks information that would be by itself sufficient to recover any core secret of any user.
Privacy
Anastasis does not safe any data from the user except for the few details needed for authentication and recovery of the secret. When using Anastasis, only the user is capable to recover their secrets. Users can pay anonymously for the service, and switch service providers at any time.
Upload Process Flow
Step 1 - User has a core secret
Step 2 - The core secret is split in several parts

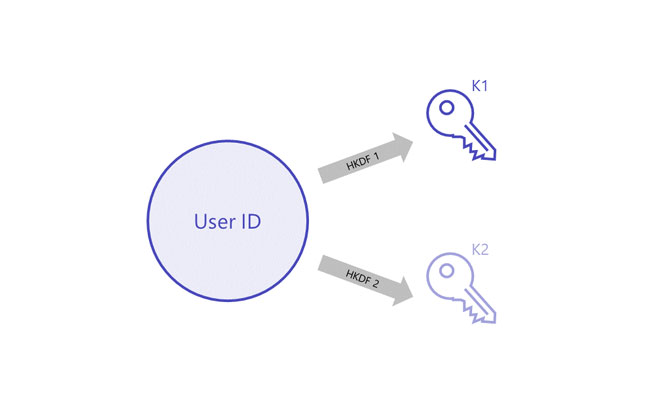
Step 3 - The system derives the User ID with the provided identity material

Step 4 - The system derives two keys with the generated user id
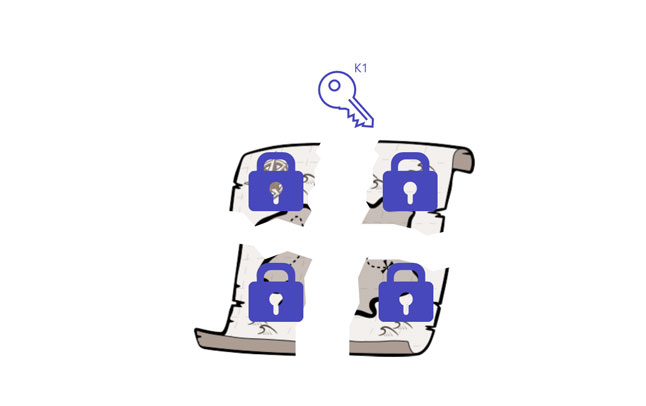
Step 5 - The pieces of the secret are encrypted with the first key
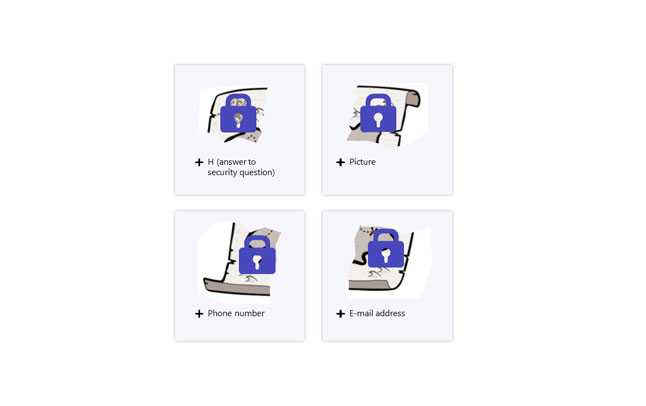
Step 6 - The user sets up authentication methods for each part of the secret
Step 7 - The authentication data is then encrypted with the second key
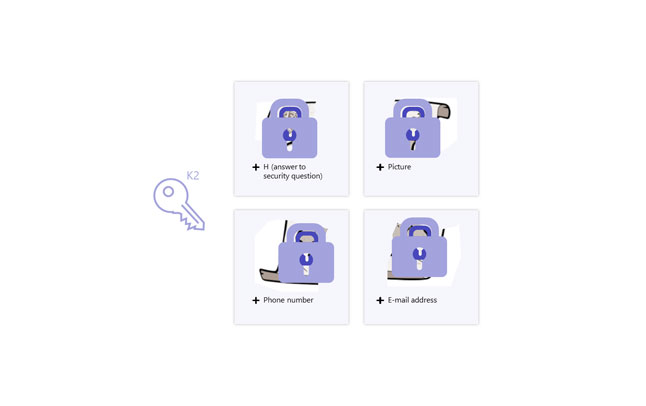
Step 8 - Encrypted shares of the recovery data are distributed to different providers
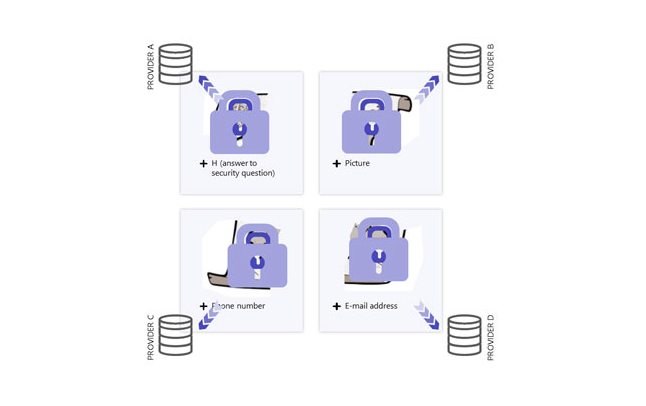
Recovery Process Flow
Step 1 - The system derives the User ID with the provided identity material

Step 2 - The system derives the same keys as per the upload

Step 3 - The user sends the second key to the providers so that they can decrypt the authentication data
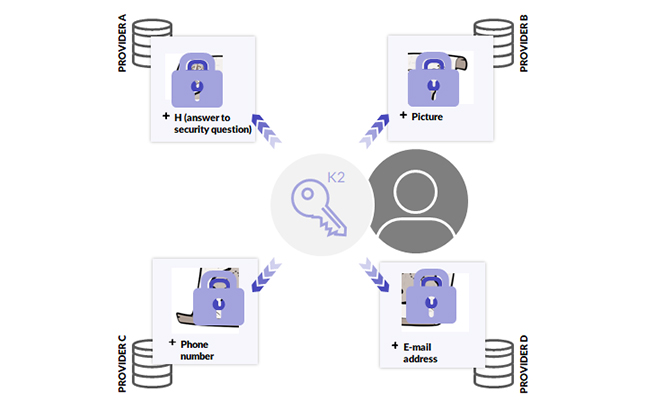
Step 4 - The providers decrypt the authentication data and issue an authorization challenge to the user
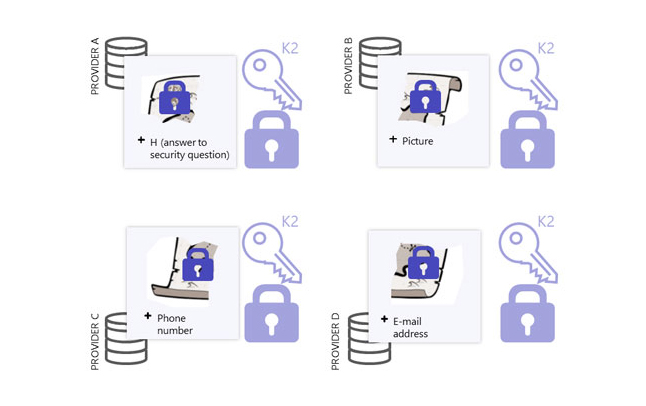
Step 5 - The user performs the different authentication procedures
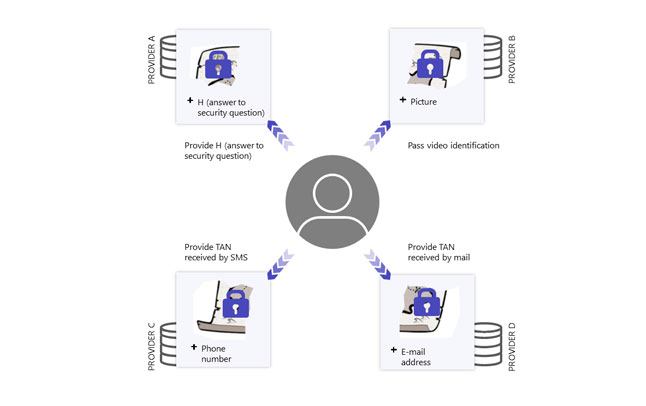
Step 6 - The user receives the parts of the secret
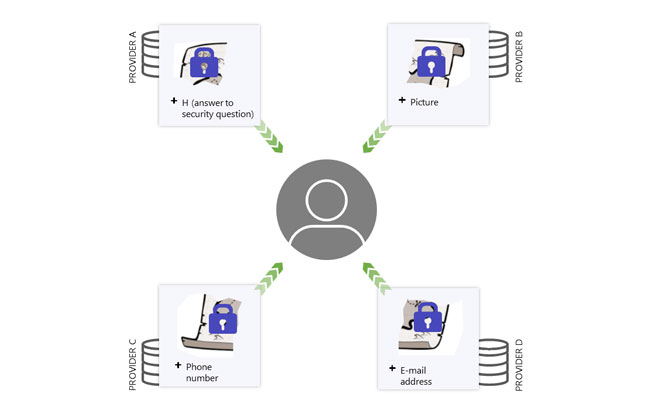
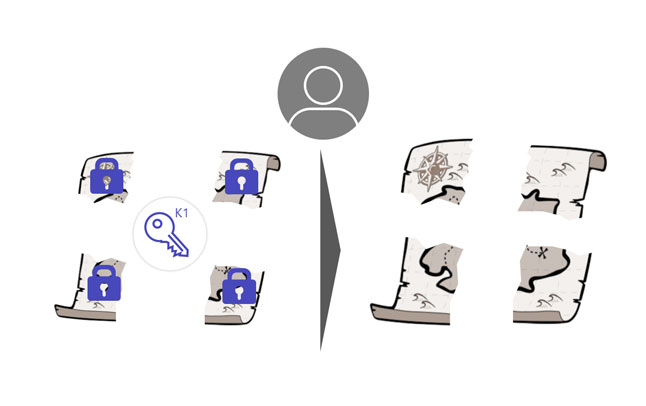
Step 7 - The user can now decrypt the parts with the first derived key
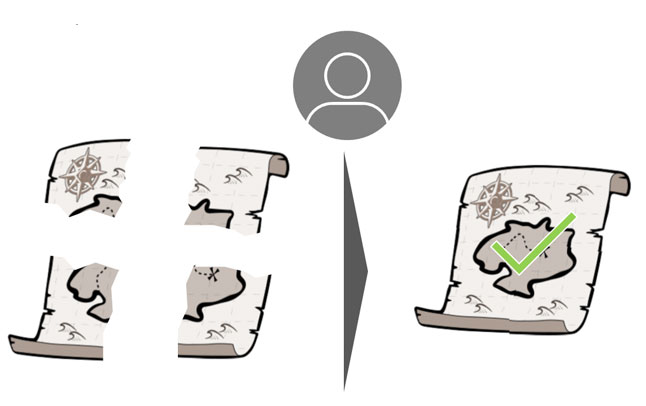
Step 8 - The system can now reassemble the secret
Unique Sales Propositions
Low-cost, scalable cloud-based solution with minimal environmental impact
Increases informational self-determination by keeping consumers in control of their data
Distributed trust instead of single point of failure
Ease of use
Generic API suitable for a range of applications
Maximum privacy with respect to authentication data
Customers can remain anonymous
Post-quantum security
E-money issuers do not need to protect customer data against own staff